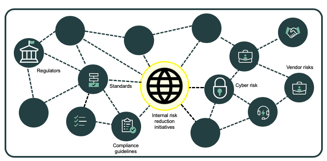
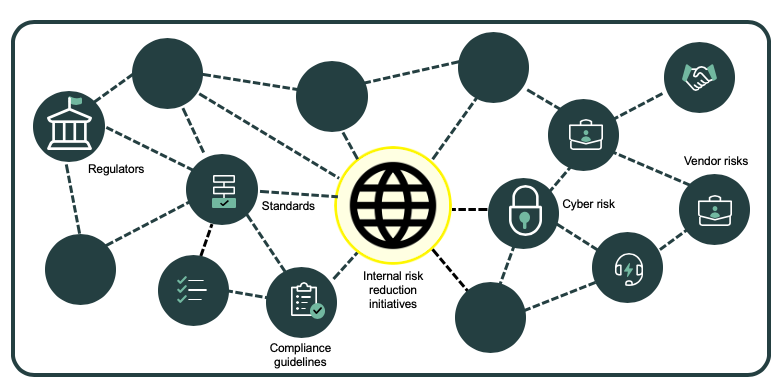
 Everyone knows. But companies and institutions find it hard to implement. No organization operates in splendid isolation. They all are embedded in networks of dependencies. More and more their connectivity has a digital component.
Everyone knows. But companies and institutions find it hard to implement. No organization operates in splendid isolation. They all are embedded in networks of dependencies. More and more their connectivity has a digital component.
Security and compliance
Our lives are depending on digital services. That makes us vulnerable. This vulnerability is a threat to all aspects of the functioning of society. Security enables the reduction of these vulnerabilities. Not just in technology, but especially in organizations and human behavior. The focus of data security is the protection of all sensitive data within the organization. But there are strong overlaps with domains like privacy, information management, compliance, business continuity, integrity and others. Information is raw material of any organization and its processes, products, and services. Loss, theft, manipulation and the invasion of privacy may seriously damage the organization, its customers and vendors and other partners in the value chain. Security and compliance frameworks often overlap, and usually just have a small number of requirements unique to the industry or data type to protect.
Cybercrime is here to stay
People understand when institutions are attacked, and measures are taken. People don’t understand if it shows that not all necessary precautions are taken to prevent data leaks of security breaks. Incidents force management to explain how they cope with standards and obligations. And that their security is organized. This is not just IT-infrastructure. It is about the protection of personal data, complying with the rules of conduct and the protection of vendor relations. It is not just the IT lock of the door, but the management of all controls of risks with a major impact.
In volume, laws and regulations grow. The mutual dependencies between these sets of rules also grows. A security breach (regulated in the BIO or ISO 27001) needs to be reported to the Dutch Data Protection authority (regulated in the GDPR). The integrity of financial reports (regulated in SOX) presupposes a properly structured IT (regulated in COBIT and ISO 27001).
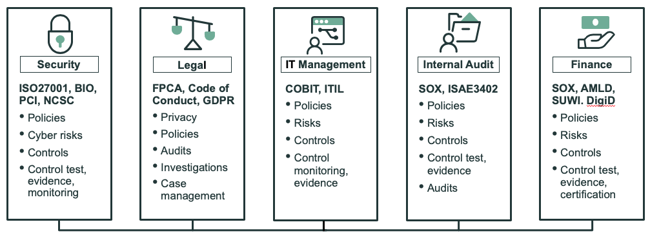
Breaking up silos
Managing controls in a manual process is a losing battle. It is just too much work, not precise, untimely, and always error prone. Don’t be surprised if the outcome of attestation questionnaires is different if it was based on real data, rather than on self-attestations. Identifying deficiencies on a quarterly, if not annually, basis, also leads to very low response.
Automation is imperative. Within individual silos, managers select different types of tooling to manage compliance and risks. But now, with growing dependencies over silos, managing controls with different technologies is burdensome. The combination of outcomes of different tools appears to be a hotbed for spreadsheets, threads of emails and many meetings.
Today’s complexity calls for a paradigm shift: a call for a single system of action. A holistic approach helps to cooperate beyond silos. This comprises:
- A universal language for data, workflows, policies, remediation of non-compliance and reporting;
- A coherent data set: a single source of truth;
- A consistent way of working: a single system of action;
- 3600 reporting to empower employees to take the right decisions: single structure of engagement.
The many different authority documents to comply with contain easy many thousands of mandates and therefor many thousands of controls. The volume explodes if controls need to be tested on a regular base, say every month of quarter.
The first benefit of the holistic approach is elimination of duplication of work. In a recent project for a non-governmental institute with control tests for BIO, DigiD and GDPR we managed to reduce the controls with over 30%. This percentage will rise with every new set of mandates to be tested – think of SUWI.
A second benefit is automation. And this is the foundation for continuous monitoring; key to compliance and risk management focused om continuity and resilience.
The road to resilience
In most cases the actual resilience of an organization is a mixed picture. Depending on structures in the organization and skills of its employees. 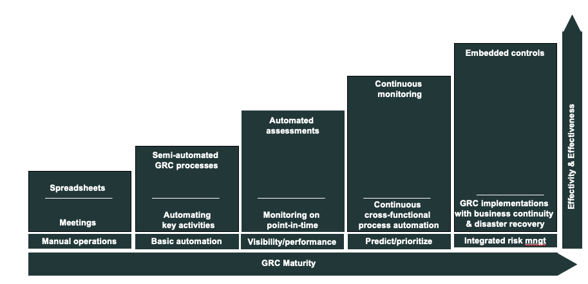
Improvements in the quality of information security is an ongoing process. It is embedded in every process using sensitive information. Quality is expressed in
- The completeness of the set of measures based on defined policies
- Effectiveness of the measures implemented
- The effectiveness of the remediation cycle in case of incidents
A solid compliance framework and automated workflows opens the perspective of continuous monitoring and direct interventions to safeguard operational continuity:
- Monitors and reduces risk exposure with real-time visibility: Get an integrated view of risk and compliance. Improve performance through better communication and reporting
- Works smarter and makes better decisions with asset context: Prioritize issues automatically. Calculate risk scores based on the severity of the issue and the importance of the asset or service to the business
- Responds faster using workflow management, automation and orchestration: Route work seamlessly between security, risk, and IT teams to reduce manual processes and hand‑offs
Let’s help you with your lock on the door (security) and design and implement your roadmap towards a resilient organization.

![Workplace-Header-2048-x-1032-wit[12] Workplace-Header-2048-x-1032-wit[12]](https://dxcservicenowbusinessgroup.com/hs-fs/hubfs/Workplace-Header-2048-x-1032-wit%5B12%5D.webp?width=1946&height=272&name=Workplace-Header-2048-x-1032-wit%5B12%5D.webp)